MEV-aware Information Technology
In my previous posts, I talked about the problems of MEV. In this article, I discuss building MEV-aware protocol can solve these problems, and point to SUAVE as a promising development to this end.
Over the holidays my dad got my sisters and I Ryze mushroom coffee, WonderCow Colostrum powder, and Tumtek selfie sticks for Christmas. One of my first reactions was, how in the world does my dad land on these gifts? “Research” he responds, followed with categorical descriptions for why each–and specifically these brands–are great. Whatever the case, I enjoyed the gifts because I’d never think of mushroom coffee, cow stomach powder, or a fancy selfie stick, for myself. And I love trying new things!
The following day, as I’m getting through crypto’s daily deluge, his assistant comes over and plops a couple sheets of paper onto his desk. They were screenshots from an Instagram reel of a clam linguine recipe. I realized, it’s likely that Instagram actuated my dad’s purchasing of those gifts by nudging him into thinking some variation of “the kids would like these” or “these would be great for the kids.” Notwithstanding whether or not we do, my dad ‘thought’ we would because some ad or influencer ( likely influenced by some other ad, influencer, or business) suggested he would, and everyone knows that when you’re gift giving, “it’s the thought that counts.”
MEV-unaware Information Technology
This interaction on the Internet–wherein information-technology predicts and actuates user behavior–happens everyday, and it’s happened for years. It’s invisible and representative of the extractive relationship between Internet corporations and users. Simply, in exchange for “free” products and services, like “Googling it” and connecting with friends on IG, users trade all their sensitive information, essentially their privacy, (including IRL interactions, voice, video, emails, payment histories, photos, contacts, and location) to corporations that have the incentive, capacity, and dominance to extract most of the value from users’ data.
But with billions of data points about all the details of our lives, data scientists can literally, actually actuate user behavior; in other words, they not only predict our behavior, but they can influence it, with surprising precision. And as these “big data” companies continue to get more entrenched, their ability to actuate improves to the extent at which there’s an unclear line between actuate and control. Broadly this is what Harvard business school professor Shoshana Zuboff calls surveillance capitalism, an economic concept that describes modern day capitalism as corporations collecting and analyzing data to profit from effectively actuating consumer behavior.
At a high level, this version of capitalism brings awareness to our relationship with technology and our perception of the way in which we use and are used by the Internet. And as I write this article, my goal is not to change your perspective on the Internet or capitalism (although I’d love to hear others’ perspective on this topic)! (And if you are interested, I’ll refer to this video of Jaron Lanier sharing his thoughts on why you should delete your social media accounts for a pleasant, non-exhaustive perspective on issues under this regime). Rather, I’d like to note, assuming we avoid the extreme point of view that the Internet is totalitarianism in disguise, the fact that these forces are largely unknowable–that is, there is no way to measure, or observe, prove, or disprove, the extent in which we gain or lose autonomy in our digital lives–is in and of itself a concern.
And, with the rise of AI integrating with legacy information-technologies, producing results from black boxes that we cannot interpret, it’s difficult to conceive a future in which these capitalistic structures change and the aforementioned concern diminishes in the current paradigm. In fact, to me it feels like the concern continues to grow, albeit alongside adjacent trends of self-sovereignty and distrust in older institutions.
However, it is conceivable that blockchain offers an alternative information-technology that can reprioritize users. We can install protocol that coordinates the flow of information and value, makes the value of users’ privacy and information knowable, and affects changing incentive structures between populations and corporations to cooperate toward more balanced prosperity. To this end, my intent is to illuminate that surveillance capitalism is not dissimilar to the risks that we face in MEV, and that building MEV-aware protocol can make incentives knowable and thus serve as foundation for alignment.
“Will surveillance capitalism be the hegemonic logic of accumulation in our time, or will it be an evolutionary dead-end that cedes to other emerging information-based market forms? What alternative trajectories to the future might be associated with these competing forms?”1 - Shoshana Zuboff, The Big Other (2015)
Becoming MEV-aware
If I could wave a magic wand and change anything about the Internet, I would wish that it were more privacy-aware (or MEV-aware). In my perspective, that would imply (1) regulation would force Internet corporations to be more explicit about how user data is collected, processed, and leveraged for-profit, such that we would collectively have more oversight on the extraction that takes place and construct more effective information markets. Or (2) users would have more autonomy over which data they’d like to share or keep private, from which the free market could determine the amount of value the user receives for their information.
As it pertains to crypto, the corollary of surveillance capital on blockchain is MEV. On Ethereum, every 12s future state is dictated by an increasingly concentrated set of centralized infrastructure providers. Simply, users send transactions to public or private pools from which highly sophisticated actors survey the information and opportunistically reorder, insert, or replace transactions to extract value. Like traditional information-technologies, crypto-native businesses inspect the contents of users' transactions and extract value from them. Left unchecked, without effective mechanism design, we’ll risk entrenching crypto-native institutions installing very similar power structures of traditional presets i.e. “same sh*t, different pile!”.
From this perspective, privacy-aware is essentially MEV-aware–in that both entail being conscious of the value that is extracted when a user trades their information.
Blockchain is information-technology’s second chance
It’s possible crypto can address both of my wishes: (1) we can build infrastructure and applications that give users more autonomy over their data and (2) leverage the social layer to codify more transparent MEV-aware incentive structures. Both of which can produce freer markets where information and resources can be fairly priced and, more significantly, knowable to users. In fact, we are already seeing trends toward the former—a signal crypto protocol already values becoming MEV-aware.
For instance, Flashbots released mev-share, and there are other similar products such as mev-blocker, that allows users to gain some of the value the information in their transactions create. Put differently, with mev-share, sophisticated actors can inspect a transactions’ hints, execute profitable trade(s), and give some of the profit back to the user. Already, with these basic primitives, we can observe more proper value attribution to the user than what we can expect when sending transactions to a public mempool, or just “Googling it.”
Another example is the rise of neutral builders, such as Titan builder, penguin builder, and jetbldr. These block builders compete to commoditize the edge other more sophisticated vertically integrated searcher-builders have, effectively leveling the playing field and redistributing MEV to searchers. More specifically, Titan built a bundle tracing product that gives searchers more insights into why their transactions were or were not included in their blocks. And there’s another product in beta that allows searchers to specify where they want to land in the block.
Blocknative provides additional products and services, such as ethernow, that increase observability for otherwise opaque MEV interactions, and Bloxroute builds technology that improves performance for various actors across the MEV supply chain, such as Bloxroute BDN or the Validator Gateway.
In addition, there is countless research illuminating the dark forest, enabling collaboration for counteracting the negative externalities of MEV.
The tldr is, even though MEV is temporarily centralized, there seems to be an incentive to give more autonomy to users’ privacy and democratize MEV–to become more MEV-aware–something that does not necessarily exist in other technologies. In other words, blockchains are MEV-aware, whereas the Internet is MEV-unaware. Most notably, in my opinion, Flashbots is building SUAVE.
The Future of Information-Technology is SUAVE
At a high level, SUAVE is fairly simple. It is a platform for building and using MEV applications (“SUAPPs”), such as mev-share, mev-blocker, block builders, relays, MEV-aware AMMs, and more. The design space here is vast. Essentially, it’s an open marketplace for to use SUAPPs on an EVM-compatible chain upon which the current centralized MEV supply chain can be rebuilt and repurposed in a decentralized and private way.
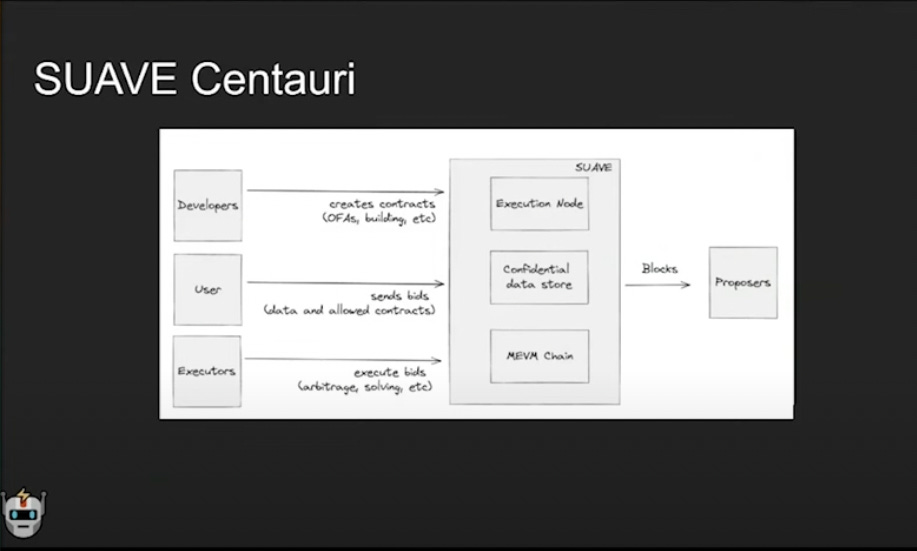
Developers can write SUAPPs, and users can access these SUAPPs and send bids with confidential data and preferences to be executed. Executors (searchers, solvers, builders) search through users' bids and compete to execute them accordingly, properly back running or inserting more transactions for MEV and returning a share of the MEV. Lastly, proposers are listening to SUAVE for blocks which they sign and publish to the EVM. Figure 1 is an outline of SUAVE’s architecture and participants.
SUAVE also introduces this concept of programmable-privacy, which means users who interact with SUAPPs can customize what information they want to share and to whom they want to share it with. Consider the following scenario: say you have 10 pieces of information that contribute to your preferences for exchanging $ETH for $SOMECOIN (or something to buy your kids for Christmas). Right now, the default is to give all our information, and if we don’t, we lose a significant amount of value i.e. we can’t access the service or get low priority. This is bad UX.
SUAVE is a system in which you can define which information you want include for this exchange and to which contracts you permit to process your information. So instead, you can choose which information you want to share and keep private. Maybe this means you permit only one block builder SUAPP, specify a minimum and/or maximum price you’re willing to pay, express strict time preferences, define certain rollups you’d like to search on, and express the amount you’re willing to pay according to a certain payout function. This allows executors to fulfill bids based on the information set you prescribe. It might start to look like SUAVE is intent infrastructure, and that’s because it is.
In aggregate, SUAVE is a platform upon which we can build decentralized MEV-applications and trade users’ intents, and offers the potential to generate private MEV-aware information markets.
Trading Information
Furthermore, given a marketplace where users have the option to trade expressions of their intent rather than completely relinquish their full intent altogether by default, users become the arbiters of their information (because they become more interested in which information they want to share and withhold) and infrastructure providers and other users competing for MEV become agents that service the most effective route for information (because they become more interested in serving users based on the information they’re given). With this setting, you can imagine more aligned incentive structures because in order to receive users’ flow (a.k.a. information), you must do so well i.e. return MEV with integrity and honesty.
Note: the key here is SUAVE (and MEV-aware protocol in general) makes the exchange of MEV more knowable.
This is different from existing information-technology in which it is unclear or unknowable exactly how users benefit from their intent or information, while, on the other hand, it is very clear infrastructure providers extract value hand over fist. In other words, who knows how much my sisters will like the mushroom coffee, colostrum powder, and selfie stick, but we do know my dad paid someone.
The Middle Ground is Better Ground
Taking a step back, it is impossible to imagine a world where all users benefit perfectly from their data because in order for a user to gain value from a service or product, they must purchase it or trade information. Essentially, when information flows, someone loses, unfortunately. Otherwise, the system risks collectively losing the incentive to innovate better products and services i.e. value attributable to being MEV-aware must be displaced from somewhere else. Another way to think about this within the confines of MEV is, if MEV-aware systems drive searchers’ (or other rent-extractors) revenue down to zero, such that users gain all of the value, what is the incentive for them to perform more important tasks such as liquidating bad debt? Asked differently, what value does MEV-aware value displace? Outside MEV, who will innovate the selfie stick market?
But there is a middle ground somewhere between corporations taking all the value and users keeping all the value.
Another relevant question is, do users even care about their personal data or privacy? Honestly it’s possible the average user doesn’t. My dad happily scrolls through IG, and my friends still love Tik-Tok. And given the amount of sandwiching that happens on-chain and ape’s willingness to secede their private keys, it’s not clear users care either.
Or, is it that we just aren’t aware? Further, are we not aware of the value of our information and digital autonomy because there isn’t an incentive to build or use alternative systems and become aware? Perhaps we are actuated into this status quo.
"Can we come up with a power distribution that doesn't collapse decentralization, can we maintain permissionlessness, what are the best economic mechanisms to encourage competitiveness and distribution vs more predatory rent extraction, or zero-sum games, or sniping, or something more socially wasteful?"2 - Phil Daian, Founder at Flashbots
Other questions to ponder:
Could more visibility into the exchange of users’ information produce more balanced cryptoeconomic incentives structures such that more MEV is internalized than externalized?
Is there a limit for individual expression? Who is the “state” (or set of stakeholders) that determines these boundaries or rules? And how does this group of stakeholders fairly set them?
Do users value decentralization and privacy enough to send bundles through SUAVE such that SUAVE blocks are more valuable than blocks built in centralized servers?
Will expressing and trading intents eventually lead us down the same road? How do we ensure the road is not a dead end?
What design choices do we consider that reprioritize giving autonomy to users and their information i.e. create a market for users’ information as opposed to a market of users?
It’s worth building MEV-aware protocol to address these questions and unearth the kinds of value blockchains can redistribute back to users. To this end, doing so is important to provide an area where users have more control over their privacy and the value of their information, which might yield larger implications around cryptoeconomic incentives.
If you are a developer and interested in building a SUAPP, please reach out. It’d be great to collaborate and develop more democratic cryptoeconomic systems. For more resources on SUAVE, here is a starting point for diving in, and here are some SUAPPs that were built in ETH Istanbul.
(Fwiw, to answer Shoshana’s questions from the aforementioned blocked quote, my answers are: no, yes and blockchain.)